Review of the Guidelines on Security Assessments for Data Export
Review of the Guidelines on Security Assessments for Data Export
Background
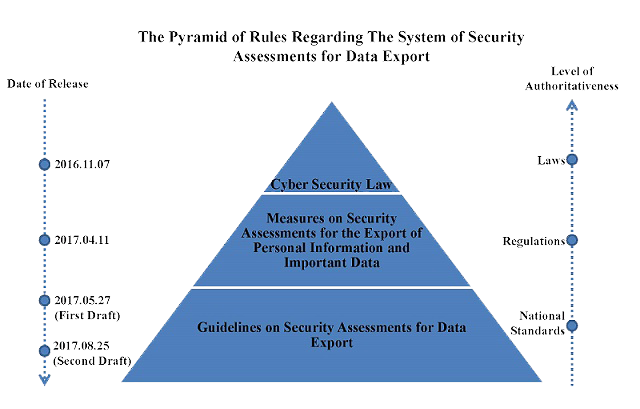
The Cyber Security Law of the People's Republic of China ("Cyber Security Law"), promulgated on 7 November 2016, has come into effect as of 1 June 2017. The Cyber Security Law for the first time subjects critical information infrastructure operators ("CIIO") to the requirements of data local storage and security assessments for data export. The Cyber Security Law also provides that security assessments shall be conducted in accordance with the measures to be formulated by the state cyberspace administration authorities in concert with the relevant departments under the State Council.
On 11 April 2017, the Cyberspace Administration of China ("CAC") released the Measures on Security Assessments for the Export of Personal Information and Important Data (Draft for Comments) (the"Measures"). Notwithstanding that only CIIOs are obligated to conduct security assessments for data export under the Cyber Security Law, the Measures has expanded the scope of the parties subject to security assessments from CIIOs to all network operators. The Measures has established the basic rules on, among other things, the scope of application, procedures, regulatory bodies, and contents of security assessments, and constructed the framework of security assessments for the export of personal information and important data.
On 27 May 2017, the National Information Security Standardization Technical Committee ("TC260") released the first draft of Information Security Technology - Guidelines on Security Assessments for Data Export[1] (Draft) (the "Guidelines"), which has stipulated the process, key items, methods of security assessments, and guidelines for identifying important data for data export. Three months later, TC260 released the second draft of the Guidelines on 25 August 2017. Comparing with the first draft, the second draft of the Guidelines has clarified the definitions of domestic operation and data export and further detailed the process of security assessments.
The TC260 is a technical working organization led by the Standardization Administration of the People’s Republic of China, which is responsible for conducting information security standardization in the field of information security technology. While the Guidelines is only a recommended national standard (GB/T), Article 17 of the Measures provides that the specific scope of important data shall refer to the relevant national standards as well as the guidelines for the identification of important data. Such guidelines for the identification of important data are included in the Guidelines as an annex. Thus, the Guidelines, as an important component of the data export security assessment system, has filled in the blanks of the specific rules left by the Cyber Security Law and the Measures regarding security assessments for data export. Moreover, the Guidelines has provided guidance for the security assessments for the export of personal information and important data, and increased the practicability of the system of security assessments for data export.
Comments on the Guidelines
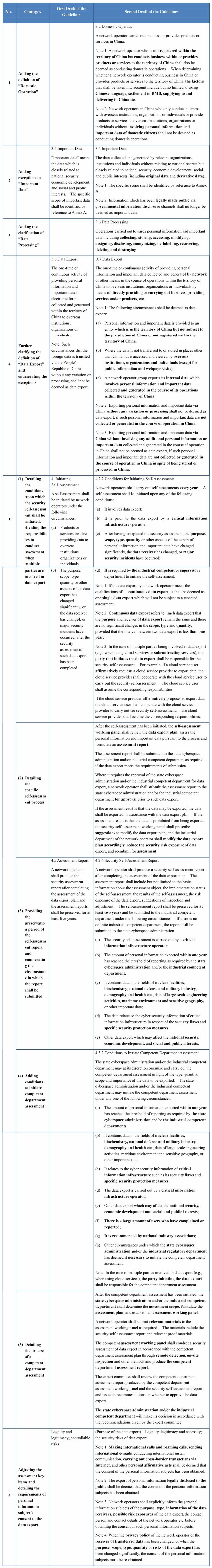
Comparing with the first draft of the Guidelines, the second draft has not made any big changes in its structure or content other than filling in the blanks left in the Measures by elaborating certain important concepts as well as detailing the security assessment procedures. Based on the basic rules of security assessments for data export as constructed by the Measures, the second draft of the Guidelines has clarified the scope of application of security assessments for data export and made the security assessment system more feasible and practicable. The second draft of the Guidelines has the following four highlights:
1
It has responded to certain controversial issues in the data export practice and further clarified the scope of application of security assessments for data export.
The second draft of the Guidelines has provided further definitions of "domestic operation" and "data export" and specified the circumstances in which disputes might occur in the data export practice, which makes the scope of application of data export clearer. For example, as far as the definition of "data export" is concerned, on one hand, the second draft of the Guidelines includes the following three circumstances into the scope of "data export":
(1) where personal information and important data is provided to an entity which is in the territory of China but not subject to the jurisdiction of China or not registered in China;
(2) where the data is not transferred to or stored in places outside China but is accessed and viewed by overseas institutions, organizations and individuals (except for public information and webpage visits);
(3) where a network operator within its group exports its internal data which involves personal information and important data collected and generated in the course of its operation in China.
On the other hand, the second draft of the Guidelines excludes the following circumstances from the scope of "data export":
(1) where the personal information and important data that is not collected or generated in the course of operation in China is exported via China without any variation or processing;
(2) where the personal information and important data that is not collected or generated in the course of operation in China but stored or process in China is exported without involving any additional personal information or important data collected and generated in the course of operation in China.
2
It has detailed the requirements of obtaining consent by personal information subjects for data export.
The second draft of the Guidelines requires that, prior to obtaining consent from personal information subjects whose personal information will be exported, a network operator must expressly notify the personal information subjects of the purpose, data type, receiver’s conditions, the possible risk exposure of such data export, the contact person and contact information of such operator etc. When there is a change in the privacy policy of the network operator or change of the receiver of exported data, or there is a major change in the purpose, scope, type, quantity or risk exposure of the data export, consent must be re-obtained from the personal information subjects.
In addition, the second draft of the Guidelines expressly points out that the following circumstances shall be deemed as having obtained the consent from the personal information subjects in data export: (1) making international calls and roaming calls, sending international e-mails, conducting international instant communication, carrying out cross-border transactions via Internet, and other affirmative personal acts; and (2) exporting the personal information that has been legally disclosed to the public.
3
It has cleared the rules of identifying the subjects who are responsible for security assessments in the case of multiple parties being involved in data export.
The second draft of the Guidelines has clarified that in the case of multiple parties being involved in data export (e.g., when using cloud services or subcontracting services), the security assessment responsibilities shall be identified according to the party which initiates the data export. For example, if a cloud service user on its own initiative requests a cloud service provider to export data, the cloud service user shall assume the responsibilities to conduct the security self-assessment, and the cloud service provider shall cooperate with the cloud service user to carry out the assessment. If the cloud service provider on its own initiative proposes to export data, the cloud service provider shall assume the corresponding responsibilities, and the cloud service user shall cooperate with the cloud service provider to carry out the security self-assessment. With these rules, it will avoid the situation in which the cloud service user and the cloud service provider both make excuses to weasel out of their respective assessment responsibilities or repeatedly conduct security assessments.
4
It has detailed the process of security assessments and set forth the differences between self-assessments and competent department assessments in the starting conditions, composition of the assessment panel, assessment reports and assessment process.
In addition to having respectively clarified the process of self-assessment and competent department assessment, the second draft of the Guidelines has enumerated the conditions upon which security self-assessments and competent department assessments will be initiated, and the circumstances in which self-assessment reports shall be submitted to the state cyberspace administration and/or the industrial competent departments. It is worth noting that the Measures has also enumerated the circumstances in which network operators shall apply to the industrial competent or supervisory departments to organize security assessments. Compared with the Measures, the second draft of the Guidelines has added two more conditions upon which competent department assessments will be initiated: (1) a large amount of users have so complained or reported; or (2) national industry associations have so recommended. These two conditions may increase the feasibility for competent departments to initiate security assessments in response to the feedbacks of the public.
Comparison between
the Guidelines and Measures

Comparison between
the two draft Guidlines
P.S
[1] The official translation by the National Information Security Standardization Technical Committee of the rule is "Information Security Technology – Guidelines for Data Cross-Border Transfer Security Assessments".
This writing was first published by LexisNexis titled "The Implementing Rules of Cyber Security Law - Review of the Guidelines on Security Assessments for Data Export (The 2nd Draft for Comments)" as well as the Lexis Wechat public account 律商视点 on 30 October 2017.
特别声明:
以上所刊登的文章仅代表作者本人观点,不得视为北京市中伦律师事务所或其律师出具的任何形式之法律意见或建议。如您有意就相关议题进一步交流或探讨,欢迎与本所联系。









